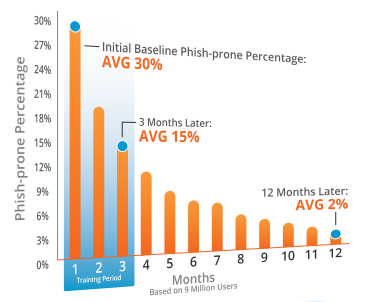
A good example and one we see regularly is CEO fraud where the victim receives an email from what looks like is their boss with the attacker asking for an urgent funds transfers. The scary part is they seem to know when your boss is out of the office! Our partner has a free test […]
Monthly Archives: February 2020
Keyloggers refer to malware installed on your computer and used to capture keystrokes from the keyboard. The information is sent to the hacker’s server who will extract passwords and other credentials.
In session hijacking, the phisher exploits the web session control mechanism to steal information from the user. In a simple session hacking procedure known as session sniffing, the phisher can use a sniffer to intercept relevant information so that he or she can access the Web server illegally. By scanning your website we can detect pages […]
Join us Wednesday, March 4 @ 19:00 (GMT), for a live demonstration of how Middlewave introduces a new-school approach to security awareness training and simulated phishing. See how easy it is to train and phish your users: Train your users with access to the world’s largest library of awareness training content and automated training campaigns with scheduled reminder emails. […]
A U.S. Natural Gas Operator Shuts Down for 2 Days After a Phishing Attack Infects it With Ransomware Dan Goodin at Ars Technica reported something worrisome: “A US-based natural gas facility shut down operations for two days after sustaining a ransomware infection that prevented personnel from receiving crucial real-time operational data from control and communication […]
Last December, a ransomware infection of Albany, New York-based accounting firm BST & Co. CPAs LLC exposed the confidential data of their customers, causing a data breach for one of their health care customers as well as other clients of the firm. Some of the data has shown up on the publicly accessible website of […]
Hackers have posted on an underground forum the personal information of 10.6 million MGM Resorts guests, ZDNet reports. The exposed information includes full names, home addresses, phone numbers, emails and dates of birth, according to the report, which claims the authenticity of the data has been verified with the help of a yet-to-be-launched monitoring firm called Under […]
Phishing is the process of attempting to acquire sensitive personal information such as account details e.g. usernames, passwords and credit card details by masquerading as a trustworthy source using emails which evade your organization’s spam filters. Emails claiming to be from your colleagues, social media sites, Microsoft etc. are commonly used to trick you into thinking […]
(February 14 & 17, 2020)Computer systems belonging to the Redcar and Cleveland Borough Council (UK) were infected with malware. The attack occurred on February 8, and as of February 26, were still “working with a reduced capacity”. The council has called in help from the National Cyber Security Centre (NCSC). The council has not said […]
According to the PCI Standards the goals of penetration testing are: 1.To determine whether and how a malicious user can gain unauthorized access to assets that affect the fundamentalsecurity of the system, files, logs and/or cardholder data. 2.To confirm that the applicable controls required by PCI DSS—such as scope, vulnerability management,methodology, and segmentation—are in place. […]
- 1
- 2